13 Nmap commands used by network administrators
Nmap (Network Mapper) is a security scanner. It is used to discover hosts and services on a computer network. Here are some commands to help you with the same.
1. Scan a single host or an IP address (IPv4)
nmap 192.168.0.1 //Scan a single IP address nmap server2.techniqa.com //Scan a host-name nmap -v server2.techniqa.com //Scan a host-name for more information
2. Scan multiple IP address or subnet (IPv4)
nmap 192.168.0.1 192.168.0.2 192.168.0.3 nmap 192.168.0.1,2,3
You can scan a range of IP address too:
nmap 192.168.0.1-20
You can scan a range of IP address using an asterisk wildcard:
nmap 192.168.0.*
Finally, you scan an entire subnet:
nmap 192.168.0.0/24
3. Read list of hosts/networks from a file (IPv4)
The -iL option allows you to read the list of target systems using a text
file. This can be useful when scanning a large number of hosts/networks. Create a
text file as follows:
cat > /var/test.txt
Sample outputs:
server2.techniqa.com
192.168.0.0/24
192.168.0.1/24
172.16.0.3
localhost
The syntax is:
nmap -iL /tmp/test.txt
4. Excluding hosts/networks (IPv4)
When scanning a large number of hosts/networks you can exclude hosts from a scan:
nmap 192.168.0.0/24 --exclude 192.168.0.5 nmap 192.168.0.0/24 --exclude 192.168.0.5,192.168.0.254
Or exclude list by creating a file in any location containing the IP's to be excluded. My file happens to be in this location /var/unnecessary.txt
nmap -iL /tmp/scanlist.txt --excludefile /var/unnecessary.txt
5. Turn on OS and version detection scanning script (IPv4)
nmap -A 192.168.0.225 nmap -v -A 192.168.0.1 nmap -A -iL /var/scanlist.txt
6. Find out if a host/network is protected by a firewall
nmap -sA 192.168.0.225 nmap -sA server2.techniqa.com
7. Scan an IPv6 host/address
The -6 option enables IPv6 scanning.
The syntax is:
nmap -6 IPv6-Address-Here nmap -6 server2.techniqa.com nmap -6 2416:c0d1:3102:22::3 nmap -v A -6 2416:c0d1:3102:22::3
8. Scan a host when protected by the firewall
nmap -PN 192.168.0.1 nmap -PN server2.techniqa.com
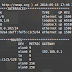
9. Scan a network and find out which servers and devices are up and running
This is known as host discovery or ping scan:
nmap -sP 192.168.0.0/24
Sample outputs:
Host 192.168.0.1 is up (0.00035s latency).
MAC Address: B4:3F:34:A2:5B:F3 (Unknown)
Host 192.168.0.2 is up (0.0038s latency).
MAC Address: 33:4A:21:4B:D7:E3 (Unknown)
Host 192.168.0.5 is up.
Host alias04 (192.168.0.12) is up (0.0091s latency).
MAC Address: 00:11:22:33:44:FF
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.80 second
10. Perform a fast scan
nmap -F 192.168.0.1
11. Show the reason a port is in a particular state
nmap --reason 192.168.0.1 nmap --reason server2.techniqa.com
12. Only show (possibly) open ports
nmap --open 192.168.0.1 nmap --open server2.techniqa.com
13. Show all packets sent and received
nmap --packet-trace 192.168.0.1 nmap --packet-trace server2.techniqa.com
13 Nmap commands used by network administrators
 Reviewed by Unknown
on
09:38:00
Rating:
Reviewed by Unknown
on
09:38:00
Rating:
 Reviewed by Unknown
on
09:38:00
Rating:
Reviewed by Unknown
on
09:38:00
Rating:





No comments: